
Allow access control and login permission only to registered faces.
AI service that verifies user identity through facial recognition.

Allow access control and login permission only to registered faces.
AI service that verifies user identity through facial recognition.
FUNCTION
The face registered upon application is compared for similarity and matched with the user’s face in real-time to confirm identity.
- Used by Financial Institutions and General Companies
- Elements Required for Identification: Your Face
- Usage: Registration of face and identification (multiple use)
TECHNOLOGIES
Face Recognition

- Real-time face detection and recognition from images and videos
- Developed an independent neural network (Independent research and development)
- Neural network learning (deep learning) and functional test using Face Set
Similarity Analysis
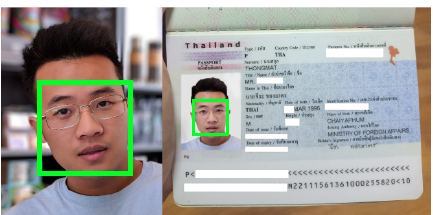
- Contrast the photo taken with the ID card
- Compare faces recognized during registration and verification process
- Analyze the similarity between both faces using artificial intelligence-based neural network learning (deep learning)
Face Authenticity Detecting Neural Network

- Preventing users from performing face registration with images and videos
- Supports facial recognition and confirmation limited to real face only
PROCESS
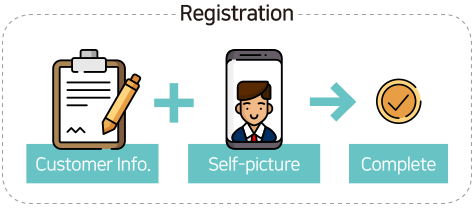
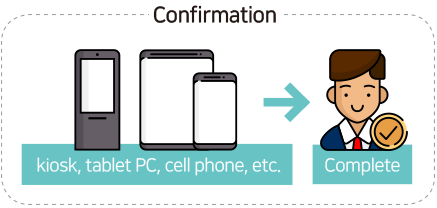
- Registration: Initial face registration, data is converted and stored as vector
- Verification: Face identification through devices with camera (similarity with initially registered face will be analized)
- Real time shooting can be checked through ActiveLiveness (mouth, head movement prompts, etc.)
- Can be used as a separate identification method or additional means of identity verification
PROCESS


- Registration: Initial face registration, data is converted and stored as vector
- Verification: Face identification through devices with camera (similarity with initially registered face will be analized)
- Real time shooting can be checked through ActiveLiveness (mouth, head movement prompts, etc.)
- Can be used as a separate identification method or additional means of identity verification
FEATURES
Compatible with cloud environment and offers independent server development
Easily connect through URL without the need of installing separate app
APPLICATION FIELDS
- Identify customers and visitors in carpooling, shared offices, self checkout stores and libraries
- Compare the participants of conferences and seminars with pre-registered information
- Identity verification for purchasing limited quantity of services and products (e.g. concert tickets)
- Employee attendance tool in a company
USER INTERFACE
The entire process of identity verification is customizable according to the user’s policy
- Able to check the request / progress / result of identity verification
- Manage the statistics and data of identity verification history
- Ease of access based on convenient UI and UX
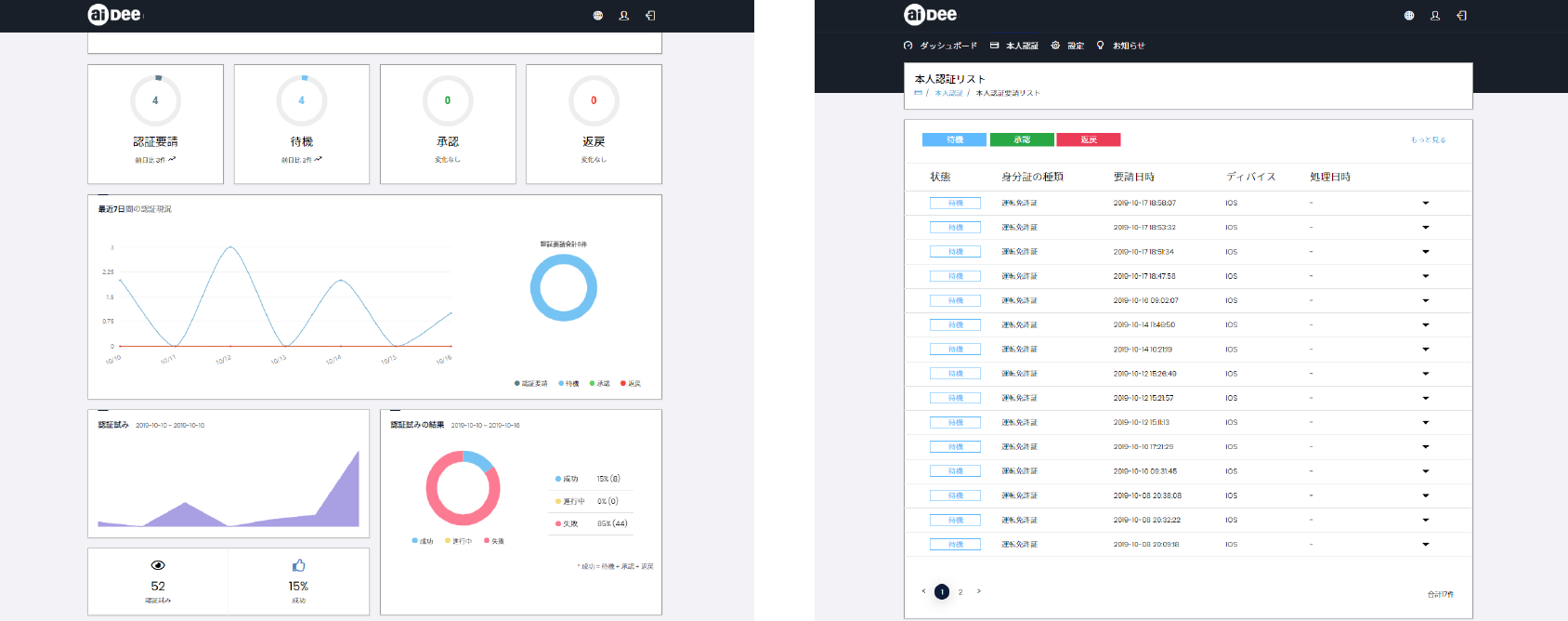
USER INTERFACE
The entire process of identity verification is customizable according to the user’s policy
- Able to check the request / progress / result of identity verification
- Manage the statistics and data of identity verification history
- Ease of access based on convenient UI and UX





